In today’s fast-paced digital landscape, cybersecurity has become an essential foundation for every organization. From IT professionals to small business owners, protecting sensitive data and critical infrastructure is no longer optional—it’s survival. With the rise of sophisticated cyberattacks, having the right set of tools ensures resilience, compliance, and operational continuity.
Why Cybersecurity Tools Matter: The Growing Threat Landscape
In 2023 alone, IBM reported that cyber incidents cost businesses worldwide over $10.5 trillion. Ransomware, phishing, and supply chain attacks dominate headlines. According to Cisco, misconfigurations and lack of layered defenses remain the top causes of breaches. This underscores why organizations must adopt robust cybersecurity solutions.
Top 5 Cybersecurity Tools You Should Use
1. Next-Generation Firewalls (NGFW)
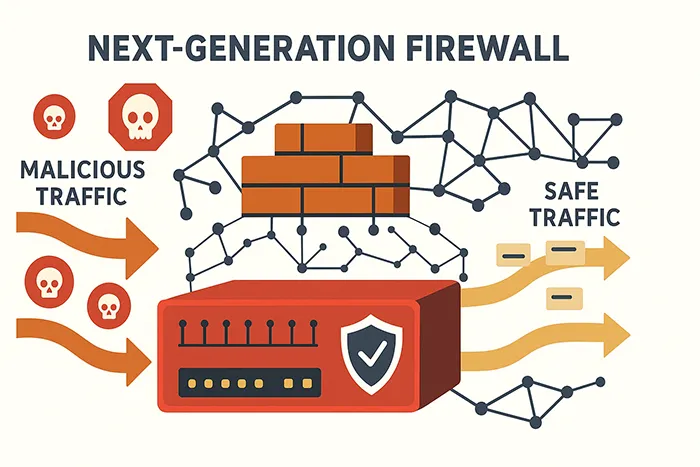
Next-Generation Firewalls offer application awareness, intrusion prevention, and real-time threat intelligence. Unlike traditional firewalls, NGFWs detect and block sophisticated cyber threats, making them the first line of defense.
- Palo Alto Networks: Industry leader with advanced threat prevention.
- Cisco Firepower: Provides strong integration with enterprise networks.
- Fortinet FortiGate: Cost-effective and scalable for SMBs and enterprises.
2. Endpoint Detection & Response (EDR) Tools
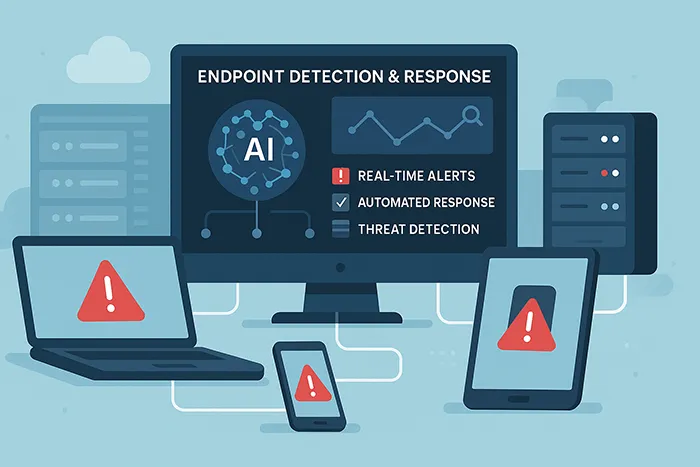
EDR solutions monitor devices for unusual behavior and automate responses. They help security teams detect, contain, and mitigate threats quickly before they escalate.
- CrowdStrike Falcon: Real-time detection and advanced threat hunting.
- SentinelOne: Autonomous detection and response platform.
- Microsoft Defender for Endpoint: Integrated into Microsoft 365 for holistic protection.
3. Data Loss Prevention (DLP) Tools

DLP solutions ensure that confidential data is not lost, misused, or accessed by unauthorized individuals. In industries like healthcare and finance, they are crucial for compliance with HIPAA and PCI DSS.
- Symantec DLP: Granular data controls and comprehensive reports.
- Forcepoint DLP: AI-powered behavioral monitoring.
- Digital Guardian: Protects intellectual property and trade secrets.
4. Security Information and Event Management (SIEM) Tools
SIEM platforms aggregate logs, detect anomalies, and generate alerts. They provide a unified view of your entire IT ecosystem, making compliance and incident response more efficient.
- Splunk: Market leader with powerful data analytics capabilities.
- IBM QRadar: Seamlessly integrates with diverse systems.
- LogRhythm: Prioritizes compliance-focused threat detection.
5. Multi-Factor Authentication (MFA) Tools

MFA solutions provide layered verification methods like SMS codes, biometrics, or authenticator apps. As passwords alone are insufficient, MFA drastically reduces unauthorized access risks.
- Authy: Simple MFA setup for individuals and small businesses.
- Duo Security: Adaptive MFA and phishing-resistant protection.
- Okta MFA: Integrated with identity management for enterprise use.
Comparison Table: Top Cybersecurity Tools
| Tool | Key Features | Pros | Cons |
|---|---|---|---|
| NGFW | Advanced firewall, application awareness | Strong real-time protection | Higher cost for SMBs |
| EDR | Real-time monitoring & response | Protects endpoints effectively | Resource-intensive |
| DLP | Prevents sensitive data leaks | Ensures compliance | Complex to configure |
| SIEM | Aggregates logs and anomalies | Centralized visibility | Requires skilled staff |
| MFA | Multi-factor verification | Strong identity security | User training needed |
Layered Cybersecurity Defense Strategy

No single tool can guarantee complete protection. Experts recommend implementing a layered defense—combining NGFW, EDR, DLP, SIEM, and MFA. This approach reduces single points of failure, enhances detection, and ensures compliance.
Expert Recommendations
- Regular Updates: Keep tools patched against the latest vulnerabilities.
- Employee Training: Educate staff on phishing, ransomware, and cybersecurity best practices.
- Layered Defense: Combine multiple tools for stronger resilience.
Final Thoughts
Cybersecurity is not about achieving 100% safety—it’s about building resilience. By leveraging these five tools, businesses can drastically reduce risks, secure sensitive data, and build customer trust. Whether you’re a startup or enterprise, these tools offer scalable protection to match your needs.
Frequently Asked Questions
What is the most important cybersecurity tool?
While all are crucial, most experts recommend starting with a Next-Generation Firewall (NGFW) as the foundation of any security strategy.
How does Multi-Factor Authentication (MFA) enhance security?
MFA requires multiple forms of verification, reducing the likelihood of unauthorized access.
Do I need all five cybersecurity tools?
For full protection, it’s best to implement a layered defense with NGFW, EDR, and MFA as minimum requirements.