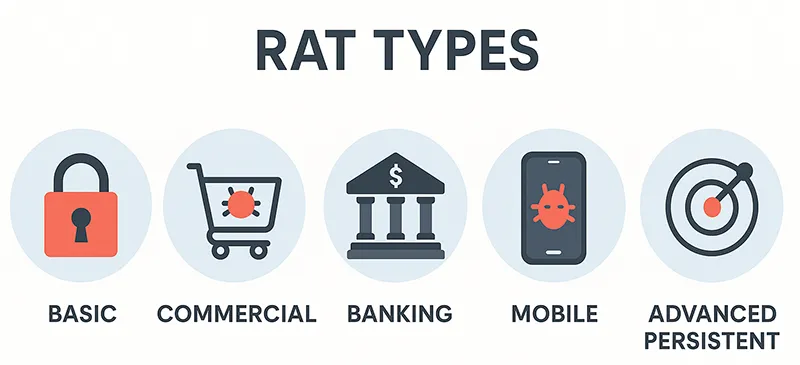
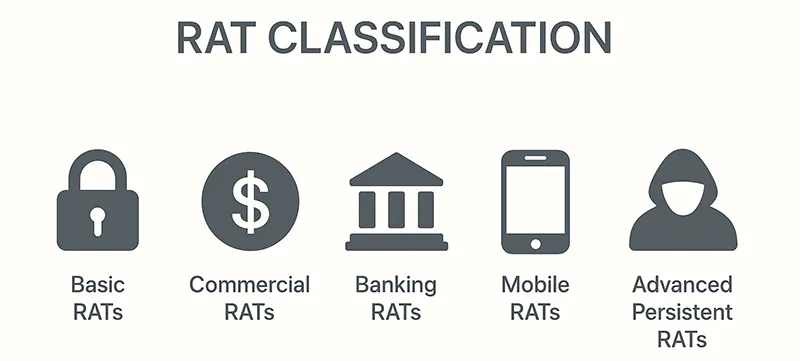
Diverse Types of Remote Access Trojans
- Basic RATs: Entry-level malware often used by amateur hackers. Example: Beast Trojan.
- Commercial RATs: Sold on underground forums with advanced features. Example: BlackShades.
- Banking RATs: Designed to steal financial credentials. Example: Zeus Trojan.
- Mobile RATs: Target Android and iOS devices. Example: SpyNote.
- Advanced Persistent RATs: Used in cyber-espionage and nation-state surveillance. Example: Gh0st RAT.
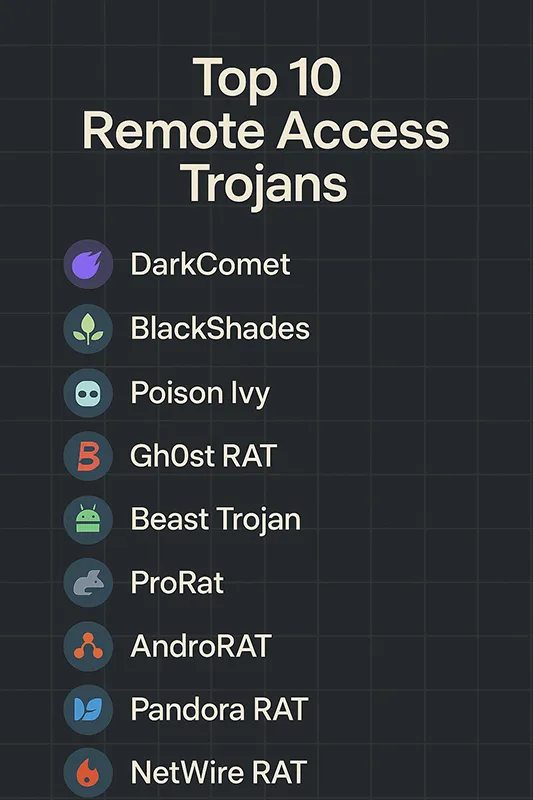
Top 10 Remote Access Trojans You Should Know
- DarkComet: Known for webcam spying and remote desktop control. Widely used during the Syrian conflict.
- BlackShades: Popular for keystroke logging and file theft. Taken down by the FBI in 2014.
- Poison Ivy: Often used in corporate espionage attacks, enabling stealthy long-term access.
- Gh0st RAT: Famously linked to government espionage campaigns in Asia.
- Beast Trojan: One of the earliest RATs with reverse connection capability.
- ProRat: Generates its own server executable, easy for attackers to deploy.
- AndroRAT: Built for Android, capable of SMS interception and call spying.
- Pandora RAT: Can install additional malware once inside a system.
- NetWire RAT: Cross-platform RAT active for over a decade, targeting businesses worldwide.
- Flame (Flamer): A sophisticated espionage toolkit with modular spying features.
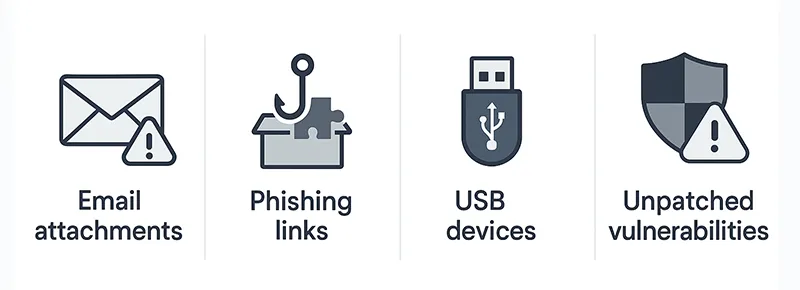
How RATs Infect Computers
- Email Attachments: Malicious files disguised as invoices, resumes, or software updates.
- Phishing Links: Fake websites that trigger RAT downloads when clicked.
- Bundled Software: RATs hidden in cracked games or free apps.
- USB Devices: RATs spreading through infected flash drives.
- Exploiting Vulnerabilities: Attackers target unpatched software or operating system flaws.
How to Protect Yourself from RATs
- Update your OS and apps regularly with security patches.
- Use Microsoft Defender or trusted antivirus tools.
- Avoid suspicious email attachments or cracked software.
- Monitor Task Manager for unusual processes.
- Enable a firewall to track inbound and outbound connections.
- Turn on two-factor authentication where possible.

What’s New Since This Article Was Published?
In 2025, new RAT variants are emerging that use AI to disguise themselves as legitimate processes. Mobile RATs like SpyNote continue to evolve, targeting both Android and iOS users. Cybersecurity experts recommend using AI-powered detection systems and stronger endpoint monitoring to stay ahead of these threats.
See Also
- Protecting Your Personal Computer from Remote Access Trojans
- Comprehensive Guide to Removing Malware
- How to Remove Malware and Viruses
- Types of Malware and How They Infect Your Computer
Frequently Asked Questions
What is a Remote Access Trojan (RAT)?
A RAT is a form of malware that allows attackers to secretly control your computer remotely, steal data, and spy on your activity.
How do I know if I have a RAT infection?
Watch for unusual processes, sudden slowdowns, strange pop-ups, or your webcam activating without reason.
Can antivirus software detect all RATs?
Most antivirus tools can detect known RATs, but advanced variants may bypass detection. Always use updated security tools.
What should I do if I suspect a RAT infection?
Disconnect from the internet immediately, run a full malware scan, and seek cybersecurity professional help if necessary.
Are smartphones vulnerable to RATs?
Yes, RATs like SpyNote and AndroRAT target Android and iOS, making mobile security equally important.